To run your JMeter load test against a Kerberos protected HTTP endpoint can be a bit cumbersome. But when the necessary configuration is applied correctly it runs as smooth as expected.
In the following article I describe how to use and configure Apache JMeter in an environment where Kerberos authentication is required.
Kerberos in a nutshell
Since NTLM is more or less obsolete due to several security issues Kerberos is the recommended authentication service by Microsoft when you manage an Active Directory Service based (company) network.
The Kerberos protocol is based on RFC 1510 and provides authentication for a distributed network environment and is interoperable between various operating systems.
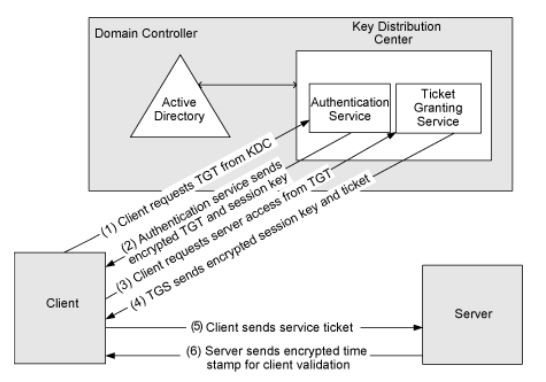
The systems core component is the Key Distribution Center (KDC) that is part of the Active Directory domain controller and performs the user authentication and ticket granting that involves the following exchanges:
- Authentication Service (AS)
- Ticket Granting Service (TGS)
- Client / Server communication (CS)
After successful authentication the requesting user will be granted a Kerberos ticket that can be exchanged with the targeting server to access its protected resources.
Configuration of JMeter
Hint: In the following samples I assume that your domain is contoso.com
To ensure that our JMeter application can make usage of Kerberos we need to provide a few settings so JMeter knows where to find the Kerberos Domain Controller and which domain realm should be used.
There are two necessary configuration files that store those values:
- krb5.conf
- jaas.conf
You can find both files in the "/bin" directory of your Apache JMeter installation. The default files contain various sample settings and links to further explanations.
Copy both files to another location. We will reference them later. With that in mind it’s also possible to use a version control system (like Git or similar) if you want to share the settings with your load testing project. But that’s not necessary.
krb5.conf
This file contains your domain realm endpoints.
The final configuration should look similar to this:
[libdefaults]
default_realm = CONTOSO.COM
default_tkt_enctypes = aes256-cts-hmac-sha1-96,aes128-cts-hmac-sha1-96
default_tgs_enctypes = aes256-cts-hmac-sha1-96,aes128-cts-hmac-sha1-96
forwardable=true
[realms]
CONTOSO.COM = {
kdc = kdc.contoso.com
}
[domain_realm]
dc.contoso.com= CONTOSO.COM
.dc.contoso.com= CONTOSO.COM
The capitalized “CONTOSO.COM” is more or less a variable name. So you can name it whatever you want.
In this sample our domain controller containing the KDC is found under the DNS name “kdc.contoso.com”. If you are not sure what your current domain controller is you can execute the following command in a Windows environment or ask your domain administrator:
nltest /dsgetdc:contoso.com
jaas.config
This file contains the configuration for the Java runtime to handle the Kerberos ticket handling. In our case we are going to use a so called keytab file to store the principal information of the account we are going to use in our load test.
This file contains the credentials in a encrypted format but you should keep in mind that anyone who has access to that file can impersonate that user. So treat the keytab file like you would with a protected password phrase.
In short the keytab file empowers JMeter to send the encrypted password to the Kerberos KDC to obtain a valid ticket for that user. So it’s not necessary to store the password in the test plan file (which is a plain XML document). Anyway you should not store that keytab file in a shared location (like a Git repository).
If you share your test plan with other team members, everyone has to create that keytab file on its own initially at least once.
You can find more information about Kerberos and the usage of keytabs in this detailed blog post.
Creating the keytab file
To create the desired keytab file you have to execute the following command with your desired load test user account:
ktab -a LoadTestUser -k "C:\secure\krb5-jmeter.keytab"
You will be prompted for the password and that’s it.
Final configuration
Putting it all together in the jaas.config file:
JMeter {
com.sun.security.auth.module.Krb5LoginModule required
useTicketCache=false
doNotPrompt=true
useKeyTab=true
keyTab="C:/secure/krb5-jmeter.keytab"
debug=false
principal="LoadTestUser@CONTOSO.COM"
storeKey=true;
};
As you can see we instruct the Kerberos module to use the desired keytab file. It’s also possible to use your own domain account as long as you are logged in locally and you got a valid ticket in the ticket cache. In this case you should set useTicketCache to true.
But in this example we go further by using an additional load test account.
Configuring the JMeter load test
So finally we can put the final piece together on the load test level.
But first of all you have to reference the two configuration files in the system.properties file that is located in the /bin directory of Apache JMeter:
#Uncomment for Kerberos authentication and edit the 2 config files to match your domains
#With the following configuration krb5.conf and jaas.conf must be located in bin folder
#You can modify these file paths to use absolute location
java.security.krb5.conf=C:/kerberos/krb5.conf
java.security.auth.login.config=C:/kerberos/jaas.conf
sun.security.krb5.debug=false
If you need further debug logging regarding the Kerberos module you can set sun.security.krb5.debug to true.
After that step JMeter should be able to use Kerberos in general. As soon as a HTTP endpoint responses with a HTTP 401 and a WWW-Authenticate header containing Negotiate JMeter will try to authorize with a Kerberos ticket obtained by our configured load test user.
We just need to set the mechanism in the HTTP Authorization Manager to KERBEROS:

Running the load test
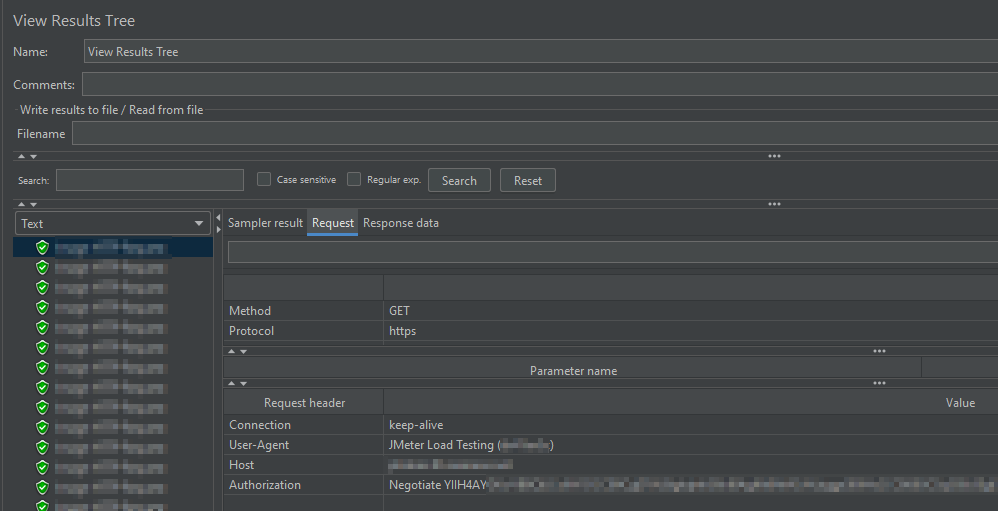
Using the “View Results Tree” component you are able to inspect the HTTP requests and can check if the Kerberos token is added to the Authorization header:
Conclusion
I made a short introduction to the general functionality of Kerberos and how to integrate it into an Apache JMeter load test by making usage of a dedicated user account by providing a keytab file.
It’s also possible to skip the keytab part and just configure Kerberos in the HTTP Authorization Manager. But keep in mind that typing a password here will store it as plain text in the load test XML file.
Overall you should now be able to understand and configure Kerberos integration with your Apache JMeter use cases.
Happy load testing! ?
Thank you very much, your guide has been very helpful. It works now as required! ?
Hi Gergo,
glad to read that it was helpful for you!
Kind regards,
Robin
Hello Robin,
Thank you for this well explained article
I followed all the steps, but I am getting the following error now:
HttpAuthenticator: NEGOTIATE authentication error: No valid credentials provided (Mechanism level: No valid credentials provided (Mechanism level: Failed to find any Kerberos tgt))
Any idea why this happened and how to resolve it please
Thank you
Hi Yones,
unfortunately I’m not able to help you directly. But it sounds like that the Keytab file containing the credentials can’t be found. You can also set the “debug” parameters to true to get additional logging.
I hope that will help you going forward!
Robin
Hi Robin,
I’m also facing the same error that HttpAuthenticator: NEGOTIATE authentication error: No valid credentials provided (Mechanism level: No valid credentials provided (Mechanism level: Failed to find any Kerberos tgt))
I set the “debug” parameters to true in the jssa.conf file and getting same response and how to create keytab file while entering the above keytab command getting ktab command is not found
Is it necessary to create the keytab file with the jaas.conf and krb5.conf
Hey Shaik,
in the described use case it’s necessary to create a keytab file. Otherwise it won’t work. That seems to be the reason why JMeter is complaining that no ticket has been provided (TGT).
It’s hard to help out here, as I don’t have access to the environment anymore where I was using that solution.
Hello Robin,
Thanks for this article.
I could apply and get it working for a single user. How did you get it working for multiple users?
Above mentioned approach a single user id – LoadTestUser is encoded in keytab or jaas.config or properties file.
How can we extend this for different user ids?
In my scenario I need to get unique user ids authenticated every time a virtual user is launched. So is there any way to dynamically handle this, like parameterizing or creating a function with user details arguments? As if we hardcode user id in supporting files, I am not sure how can multiple user authentication can be handled. Can you share your thoughts? Thanks
Hey Sourabh,
unfortunately I did not try to use a multi user account setup. I always used a single dedicated user. In case of distributed load tests we utilized multiple machines, each one using a separate user and keytab file.
I’m not aware of any solution to handle multiple Kerberos accounts in a single JMeter instance, sorry.
Noted on this Robin, please let me know if you come across any artifacts or approach on this. We are working on not only running JMeter multiuser authentication with stand alone JMeter but also incorporate JMeter with STEP platform (Software Test Execution Platform) https://step.exense.ch/ Which is an ultimate goal. Hence important to understand how multiuser Kerberos authentication would fit in this equation. Thanks for your reply anways.
Hi Sourabh,
Could you please share how you got this working? I have configured Krb5, Jaas and keytab as mentioned here. But it seems my keytab is not getting picked up
Did you perform the load test with single user???? If not can you explain how to perform load test with multiple users?